- Amerisource Business Capital Expands Team with New Regional Market Manager Appointment
- KeyBank Expands Commercial Banking Teams in Chicago and Southern California to Serve the Middle Market
- Provident Expands Commercial Lending Team as Part of Regional Growth Strategy for Eastern Pennsylvania
- Appraisers See a Mixed Picture for Valuations
- SLR Business Credit Adds Mark J. Simshauser as Senior Vice President Supporting Growth in Northeast US
What Are the Top Cybersecurity Concerns for 2022?
July 18, 2022
By Juanita Schwartzkopf
With the second half of 2022 underway, it is a good time to evaluate cybersecurity issues and concerns. The cybersecurity front continues to be an area of significant risk for businesses. In this article we will explore recent trends, and specific industries at more risk of attack. For a perspective on the dollar impact, the largest payment in 2021 was a $40 million payment made by an insurance company. For a perspective on number of attacks, there is a cyber-attack every 11 seconds.
The National Cyber Security Alliance estimated that 60% of small businesses fail within six months of an attack.
And, for companies that do survive, Cybereason, a Boston-based cybersecurity firm, estimates that 80% of victims are hit a second time.
Recent Trends
The most significant 2021 and 2022 trend is the increased number of cyber-attacks and the increased cost of those attacks.
The Numbers: Comparing the first half of 2020 to the first half of 2021 there was a 102% increase in cyber-attacks. From January to July, comparing 2021 to 2022, the FBI reported a 62% increase in year over year ransomware complaints. From January to April 2022, 4 million password stealing events (“PSW”), 35.4 million internet attacks (web page redirects, malicious programs, and botnet centers), and 47.5 million Remote Desktop Protocol attacks occurred.
The Costs: According to Paloalto Networks and their Unit 42 division, from 2020 to 2021 the average ransom demand their incident response teams dealt with increased 144% from $900,000 to $2.2 million. The average payment in 2021 increased to $541,010, for a 78% increase over 2020.
Changing Threats:
The bad actors are asking for more money and asking for it to be paid faster. Often a business is given hours rather than days before their data becomes public. The shutdowns occur immediately rather than as a threat of action if a ransom is not paid.
The attacks are resulting in multiple layers of attacks. There may be the initial shut down of operating systems, but employee data and customer or other sensitive data is then threatened with another round of ransom demands – either to the original subject of the attack or directly to employees, customers, vendors, etc.

What sectors are at the most risk?
The business sectors at most risk of cyber-attacks are healthcare, food, supply chain, energy, finance, and retail enterprises. These sectors are at risk because they have access to personal information, and they provide basic necessities such as food and shelter.
The supply chain risk includes physical infrastructure targets. For example, JBS supplies roughly 20% of the US supply of meat and in 2022 JBS paid $11 million to resolve a ransom wear attack. In 2021, an Iowa cooperative paid a $5.9 million ransom to ensure its data was protected, and the US food supply was not negatively impacted.
Examples of recent attacks related to healthcare, finance and retail enterprises include these attacks.
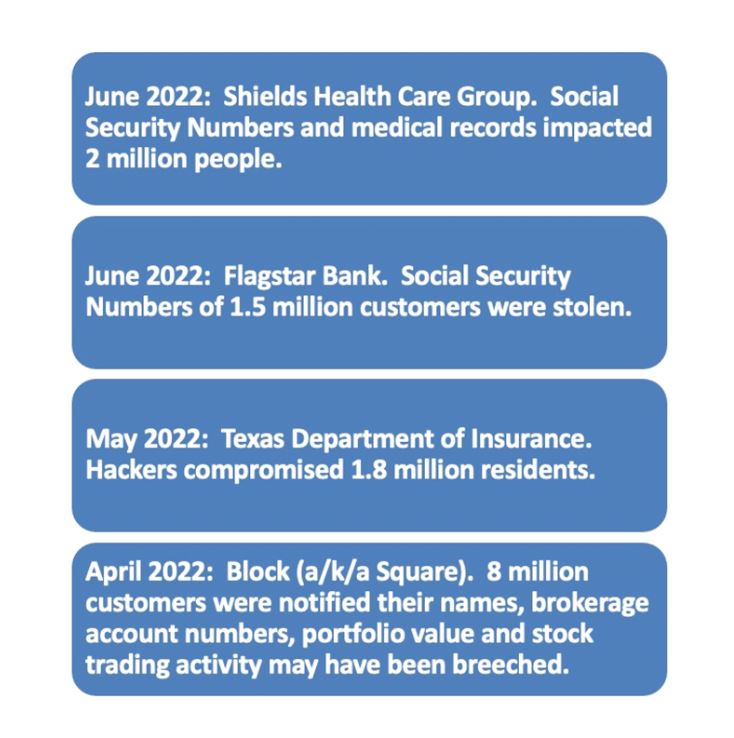
Examples of recent supply chain attacks include these situations.
 Risk Evaluation and Management: What should a business do?
Risk Evaluation and Management: What should a business do?
No system is completely fool proof. Risk management is key when considering the potential of a cyberattack. Management of a company needs to evaluate risk and consider the cost versus benefit impacts of cyberattacks compared to insurance, and systems and procedures.
First, let’s consider the IT security policy. This policy identifies the rules and procedures for all individuals accessing and using a company’s IT assets and resources. For example, this policy includes BYOD (Bring Your Own Device) policies, and password reset policies, among many other items. If a company doesn’t have an IT security policy, it needs to develop and implement one. The policy is important because it reminds employees of the part they play in protecting company assets.
Second, every company needs a disaster recovery plan. A disaster recovery (“DR”) plan contains detailed instructions for responding to natural disasters, power outages, telephone system outages, loss of access to facilities due to weather or fire, cyberattacks, and other disruptive events. An example of a disaster recovery plan is when the Iowa Coop mentioned earlier converted from electronic weigh slips and documentation to paper documentation during the crisis period. This DR plan needs to be developed and then tested. Many companies conduct regular disaster testing to ensure the plans are well developed and frequently stressed.
Industry statistics show cyberattacks may be undetected for over 200 days, allowing the attackers to hide in a network and plant malware that works its way into backup information sets as well as the active data systems. This means not only are the active data systems impacted, but also the backup systems are at risk.
Third, let’s consider backup systems. The purpose of a system backup is to provide a means to restore a computer system in the event of a hardware or software failure, a physical disaster, or human error. This process may consist of a full backup, incremental backups, or a combination of the two depending on the information and the systems. Backup processes may be onsite, offsite, or cloud based. And these processes should be tested to ensure the ability to restore the company’s systems for a comprehensive recovery of data to run the company.
An untested backup process cannot be relied on. In an emergency or stressed situation, the recovery process is aided by people who have had to perform the recovery from backup first in a test or practice environment.
Next let’s consider insurance. While cyber insurance policies are in their infancy from the perspective of standardizing coverage and the ability of insurers to meet customer needs, the cyber insurance marketplace is certainly expanding, and more and more companies need to consider coverage to meet new and changing threats.
Director and officer insurance, business interruption insurance, errors and omissions coverage, and other policies may sound like they cover parts of the cyber insurance needs, but they are not sufficient when considering proper cyber coverage risk management.
Areas to consider for coverage include:
- Data loss, data recovery and data recreation.
- Responsibility for lost or stolen customer information.
- Business interruption / loss of revenue.
- Loss of funds – wire fraud, ACH fraud, social engineering attacks.
- Computer fraud.
- Extortion / ransoms, including negotiation.
Note that typically intellectual property theft will need to be covered by a specific intellectual property insurance policy. And lost future profits are also not covered under cyber insurance.
Social engineering attacks are attacks that rely on psychological manipulation to gain access to sensitive information or company funds. These are situations where individuals follow instructions from fraudulent emails or calls, and these may not be covered under a typical cyber policy and could require a specific special policy for social engineering.
Be aware that most coverages do not cover acts of war, which could be an attack by an agent of a foreign power.
What should a business and its lender consider?
Recent cyberattacks have underscored the need for all business stakeholders to evaluate risk management related to IT systems and procedures, disaster recovery plans, backup plans, and insurance coverages.
Evaluation of a company’s approach to IT risk management is as important as evaluation of a company’s financial performance, because without a well-developed IT risk management strategy a company’s financial performance can be brought to its knees.
Every size business and every type of business is at risk for a cyberattack. Careful planning and testing are critical to survival, as is appropriate insurance coverage. Stakeholders need to add cybersecurity risk management checklists to their ever-lengthening list of risks to be concerned about.



